Advisory: put IOT devices on a separate LAN/vLAN for better security
-
@petter, When I read your reply, I notice that you are at home in this security matter.
I think many readers, even on this technical forum, are already dropping out when reading so many jargon terms ;-)As I said, how far do you want to go for your home security?
Already, with my 'simple' setup (see above), I am the only person at home who can fix it if there are 'internet' problems for the other family members.
Once everything is set up, there is the regular maintenance in the form of updates. If updates have breaking changes, then there is extra work involved to reconfigure everything, etc.In these covid times I had to face the facts, what if I drop out, what will my family members do?
I have several colleagues who also have security measures set up at home and are also SPOF or Single Point Of Failure....
I have also thought about it for my MySensors network.
Actually, that is quite a complicated setup for an outsider: sensors connect to a gateway, then, in my case, an MQTT server and then a home controller (Home Assistant), all running in VMs on the NAS.
This is also where I am the SPOF....
And the family members are already starting to rely on Home Assistant. The kids have named it Lexa ;-)So my advice, provide basic security, but don't overcomplicate it....
@evb said in Advisory: put IOT devices on a separate LAN/vLAN for better security:
@petter, When I read your reply, I notice that you are at home in this security matter.
I think many readers, even on this technical forum, are already dropping out when reading so many jargon terms ;-)As I said, how far do you want to go for your home security?
Already, with my 'simple' setup (see above), I am the only person at home who can fix it if there are 'internet' problems for the other family members.
Once everything is set up, there is the regular maintenance in the form of updates. If updates have breaking changes, then there is extra work involved to reconfigure everything, etc.In these covid times I had to face the facts, what if I drop out, what will my family members do?
I have several colleagues who also have security measures set up at home and are also SPOF or Single Point Of Failure....
I have also thought about it for my MySensors network.
Actually, that is quite a complicated setup for an outsider: sensors connect to a gateway, then, in my case, an MQTT server and then a home controller (Home Assistant), all running in VMs on the NAS.
This is also where I am the SPOF....
And the family members are already starting to rely on Home Assistant. The kids have named it Lexa ;-)So my advice, provide basic security, but don't overcomplicate it....
I get what you mean, but it's nonetheless helpful to at least have a target to aim for. Ideally there would be something entirely turn-key that one could either just buy like an appliance (as Dream Machine tried to be) or else download and run, but AFAIK neither is available yet. The problem is that quality matters, and the consumer marketplace tends to attract junk, so I'm not sure it will ever get sorted out like it should be.
-
@NeverDie You going to need an NTP Server. You can make one with an arduino nano, gps module and LAN module for under $20.
@OldSurferDude said in Advisory: put IOT devices on a separate LAN/vLAN for better security:
@NeverDie You going to need an NTP Server. You can make one with an arduino nano, gps module and LAN module for under $20.
Is an NTP truly essential?
-
as noted before you should always move IoT stuff on a own VLAN, for security purposes you should always segregate traffic as much as possible and create different security zones.
This will allow to control traffic flow with firewall rules and other systems such as IDS/IPS.
The Firewall rules controls what traffic you allow between the zones, and an IDS will control and verify that traffic. They can scan the content of a data packet and look at the content of the message or recognize applications (such as SSH over port 80 as an example)back to your question, yes PfSense is a great "enterprise grade" firewall which gives you the toolset you need such as:
- Firewall rules between zones/subnets
- 2 different IDPS systems (Snort & Suricata)
- DNS filtering & interception
- RADIUS server for mac filtering, 802.1x EAP-TLS etc.
- IGMP proxy and mDNS services for stuff like Sonos speakers etc.
so the firewall gives you the ability to control and verify the traffic, however it offers no correlation, intelligence and management. for that you use something called a SIEM (Security Information Event Management) A SIEM will capture all the logs from your firewall, switches, endpoints, mirrored traffic etc. and do correlation and analysis.
let say you have an outgoing HTTPS connection which you allowed in your firewall, (your IDS wont be able to analyze the content unless you decrypt the traffic which may break stuff). the only thing your IDS see is $&$#$&%^%*%$%^ a.k.a garbage. with a SIEM you can get open source threat intelligence etc. which will generate an alert IF a connection is made to a compromised IP/domain. A great example on a open source SIEM is Alienvault OSSIM. its an all-in-one and easy to install. Im running it as VM's in my system, together with PfSense (also VM) and some other firewalls.
If you do choose to use VM's you should use ESXi as a hypervisor. this is free, very reliable and it is what most businesses are using in their server room or datacenters. on my PfSense VM I get about 800-900 Mb/s throughput with 1 IDS enabled, so if you set it up correctly you will get the performance you need.
@petter said in Advisory: put IOT devices on a separate LAN/vLAN for better security:
If you do choose to use VM's you should use ESXi as a hypervisor.
Is ESXi essential? Basedon @monte 's recommendation above, I just recently made the leap from ESXi to Proxmox, and so far so good, including the ability to migrate VM's from one physical host to another. A bit of a learning curve, but so far it seems rock solid. The only downside I've noticed compared to ESXi is that booting from a USB isn't recommended, but that's minor.
-
I have 2 hp servers at home running esxi from an SD card, and it has been working fine for 2 years now.
I also tried proxmox for a few months, but encountered some stability issues and bugs.
Both solutions have pros and cons, but now I clearly prefer esxi.
Datastores and network are easier to manage and it is very easy to passtrought hardware to virtual machine. All the hard disks of my servers are managed by VM (Open Media Vault, Raid 5 software), without any problem.
I also use a Pfsense VM to manage all my networks, with different VLANs. It is very easy to manage VLAN under esxi with vSwitch.
In the next few weeks, I will be switching to OPNsense.
I chose this solution to mutualize the material resources, knowing that this solution can pose problems in certain cases. -
I have 2 hp servers at home running esxi from an SD card, and it has been working fine for 2 years now.
I also tried proxmox for a few months, but encountered some stability issues and bugs.
Both solutions have pros and cons, but now I clearly prefer esxi.
Datastores and network are easier to manage and it is very easy to passtrought hardware to virtual machine. All the hard disks of my servers are managed by VM (Open Media Vault, Raid 5 software), without any problem.
I also use a Pfsense VM to manage all my networks, with different VLANs. It is very easy to manage VLAN under esxi with vSwitch.
In the next few weeks, I will be switching to OPNsense.
I chose this solution to mutualize the material resources, knowing that this solution can pose problems in certain cases.@Ikes-72000 said in Advisory: put IOT devices on a separate LAN/vLAN for better security:
Datastores ... are easier to manage
Yes, I can believe that: https://forum.mysensors.org/topic/11607/best-pc-platform-for-running-esxi-docker-at-home/55?_=1617658580974
-
@OldSurferDude said in Advisory: put IOT devices on a separate LAN/vLAN for better security:
@NeverDie You going to need an NTP Server. You can make one with an arduino nano, gps module and LAN module for under $20.
Is an NTP truly essential?
@NeverDie said in Advisory: put IOT devices on a separate LAN/vLAN for better security:
Is an NTP truly essential?
I use my pfsense box as NTP relay and pass it's port in firewall rules for unsecure subnet. I don't think it can be as much a problem in home networks.
-
Originally I thought: why not just read the BIOS clock on the motherboard? Well, I suppose that would work if there were only one physical PC. For coordinating backups and file date stamps among multiple PC's, I can see how an NTP server might be helpful. I'm still doubtful absolute accuracy on a home network matters for that, as long as all the PCs sync to the same time. Then again extreme accuracy would cover all possible edge cases, including ones I can't even imagine. I could just turn the GPS clock on and forget it...forever, with no NTP port on the gateway firewall. So, after thinking it through while writing this, I can finally see how for $20 it might be worthwhile after all. For a home network you'd only need one, and it would last a lifetime.
-
Originally I thought: why not just read the BIOS clock on the motherboard? Well, I suppose that would work if there were only one physical PC. For coordinating backups and file date stamps among multiple PC's, I can see how an NTP server might be helpful. I'm still doubtful absolute accuracy on a home network matters for that, as long as all the PCs sync to the same time. Then again extreme accuracy would cover all possible edge cases, including ones I can't even imagine. I could just turn the GPS clock on and forget it...forever, with no NTP port on the gateway firewall. So, after thinking it through while writing this, I can finally see how for $20 it might be worthwhile after all. For a home network you'd only need one, and it would last a lifetime.
@NeverDie I might be missing something. What is the problem exactly to get time from the internet? Sure you may not need precise sync, but why bother yourself with GPS clock, or setting clock by hand, if every OS can pull time from public NTP severs?
-
@NeverDie I might be missing something. What is the problem exactly to get time from the internet? Sure you may not need precise sync, but why bother yourself with GPS clock, or setting clock by hand, if every OS can pull time from public NTP severs?
@monte Good question! I'm completely new to security hardening, and so I just assumed that the guy who posted the GPS NPT suggestion was aware of some threat. But if you aren't aware of one, then maybe there's no reason for it. :blush:
-
@petter said in Advisory: put IOT devices on a separate LAN/vLAN for better security:
If you do choose to use VM's you should use ESXi as a hypervisor.
Is ESXi essential? Basedon @monte 's recommendation above, I just recently made the leap from ESXi to Proxmox, and so far so good, including the ability to migrate VM's from one physical host to another. A bit of a learning curve, but so far it seems rock solid. The only downside I've noticed compared to ESXi is that booting from a USB isn't recommended, but that's minor.
@NeverDie I wouldn't.. check out this dedicated/embedded hardware.. used in many pieces of high end network appliances:
https://pcengines.ch/apu4d4.htmT.Weeks
-
@NeverDie I wouldn't.. check out this dedicated/embedded hardware.. used in many pieces of high end network appliances:
https://pcengines.ch/apu4d4.htmT.Weeks
@Thomas-Weeks said in Advisory: put IOT devices on a separate LAN/vLAN for better security:
@NeverDie I wouldn't.. check out this dedicated/embedded hardware.. used in many pieces of high end network appliances:
https://pcengines.ch/apu4d4.htmT.Weeks
You wouldn't... what? The pcengine you linked appears to be a 4 port router. What should I be learning/realizing from or doing with that piece of information? Is it meant for creating vlans or is it meant for getting the time from an atomic clock somewhere on the internet? Or something else?
-
@Thomas-Weeks said in Advisory: put IOT devices on a separate LAN/vLAN for better security:
@NeverDie I wouldn't.. check out this dedicated/embedded hardware.. used in many pieces of high end network appliances:
https://pcengines.ch/apu4d4.htmT.Weeks
You wouldn't... what? The pcengine you linked appears to be a 4 port router. What should I be learning/realizing from or doing with that piece of information? Is it meant for creating vlans or is it meant for getting the time from an atomic clock somewhere on the internet? Or something else?
@NeverDie that's not just a router it's a an x86 motherboard that you can install pfsense on. I think he meant, he wouldn't install pfsense in vm :)
It is also fairly priced, I have one of their products before, but didn't check them recently, that's a great choice for self-built firewall. -
I have an apu4d4. Started with Esxi and Opnsense in a vm, but esxi crashed when I was running a lot of traffic in opnsens. Instead I installed Debian on it and run just a basic nftables firewall. I run Proxmox on it as well. Here are performance benchmarks:
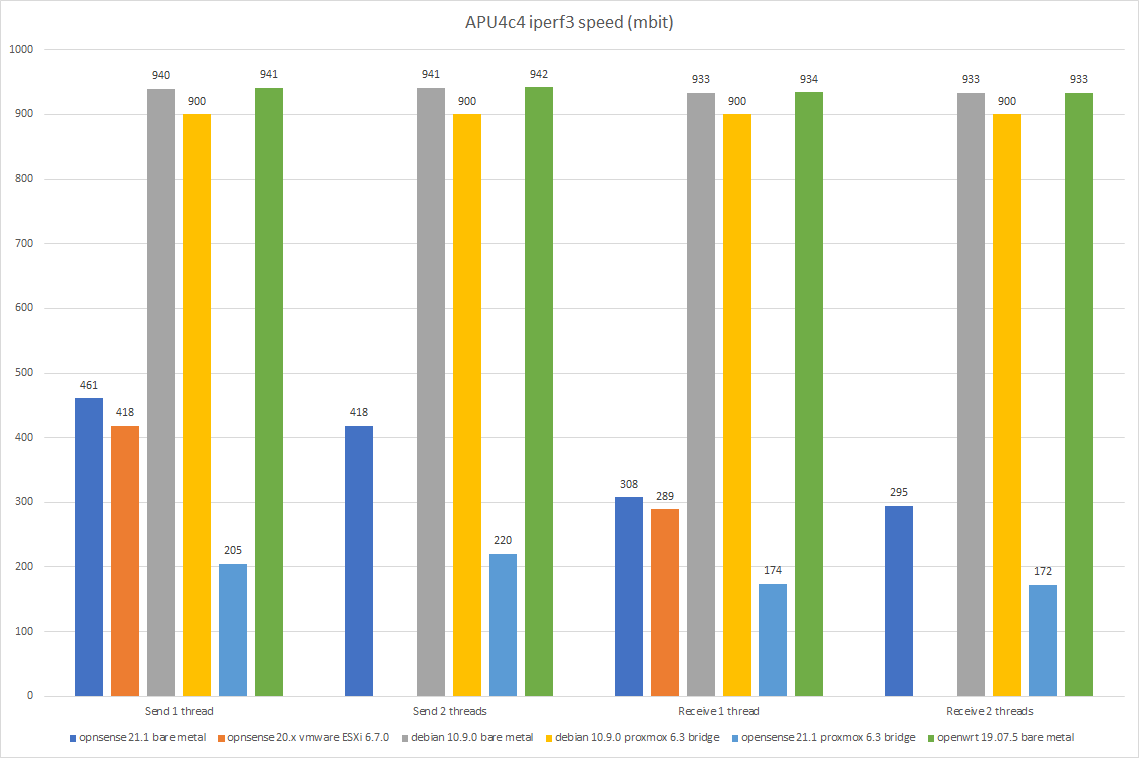
-
I have an apu4d4. Started with Esxi and Opnsense in a vm, but esxi crashed when I was running a lot of traffic in opnsens. Instead I installed Debian on it and run just a basic nftables firewall. I run Proxmox on it as well. Here are performance benchmarks:

@mfalkvidd you installed proxmox on apu4d4? I wonder why opnsense is so much slower, can it be some misconfiguration? Did you try pfsense, I'd like to know if it is any faster.
-
@mfalkvidd you installed proxmox on apu4d4? I wonder why opnsense is so much slower, can it be some misconfiguration? Did you try pfsense, I'd like to know if it is any faster.
@monte yes I did.
opnsense is so much slower because of BSD. pfsense has the same problem. I don't know the details, but it boils down to some important part of the BSD networking stack being single-threaded. It seems to be a well-known problem in the router world. I applied multiple tweaks to the BSD kernel, but they did not make any significant difference.
-
@monte yes I did.
opnsense is so much slower because of BSD. pfsense has the same problem. I don't know the details, but it boils down to some important part of the BSD networking stack being single-threaded. It seems to be a well-known problem in the router world. I applied multiple tweaks to the BSD kernel, but they did not make any significant difference.
@mfalkvidd one more question. Did you measure throughput WAN-LAN or LAN-LAN?
-
@mfalkvidd one more question. Did you measure throughput WAN-LAN or LAN-LAN?
-
Two things convinced me to have a box dedicated to pfsense (or whatever I end up using):
- @monte 's earlier advice on the subject, and
- The need for it to keep working during a lightning storm, during which I typically unplug any expensive or delicate machines but also during which I still want to maintain wifi internet access. Meaning: it could still get nuked by an electrical surge from a nearby lightning strike, but at least the replacement cost would be low. Hmmm... I suppose better still would be switching to some kind of completely wireless internet access during such storms, by maybe converting my cell phone into a hotspot or using a Verizon jetpack.... In that case, having the router be low power would be very nice indeed, because then it could run on batteries during the storm and thereby have no lightning risk at all.
-
My plan is to put pfSense onto this Supermicro motherboard, which has 6 software programmable gigabit ethernet ports plus a seventh for IPMI access:
https://www.supermicro.com/products/motherboard/atom/x10/a1srm-ln7f-2758.cfmI'm not sure what "software programmable" means in this context, but it connotes that maybe not everything needs to be routed through the CPU.
It consumes at most 20 watts when under load, but, IIRC, roughly 6 or 8 watts when idling. The Intel atom processor is built-in to the motherboard. The atom doesn't have much single thread oomph, but it does have 8 cores and all the features required to run a hypervisor, which might be worthwhile, especially if it turns out that the software programmable ethernet ports can be configured to manage all the routing on their own.
If I didn't already own this board, I'd probably pick up a similar Supermicro board that has six 10-gigabit ports on it. Right now there are a ton of used ones on ebay for around $80 per board, some including an E3-1200 processor in the $80 price. i.e. they cost even less than the pcengine board. Probably more than 20 watts TDP, but considering its a SuperMicro motherboard and each of the six ports supports RJ45 10gbe.... Heck, at that price for a 10Gbe node, I should buy 3 and build an HA ProxMox cluster.
-
My plan is to put pfSense onto this Supermicro motherboard, which has 6 software programmable gigabit ethernet ports plus a seventh for IPMI access:
https://www.supermicro.com/products/motherboard/atom/x10/a1srm-ln7f-2758.cfmI'm not sure what "software programmable" means in this context, but it connotes that maybe not everything needs to be routed through the CPU.
It consumes at most 20 watts when under load, but, IIRC, roughly 6 or 8 watts when idling. The Intel atom processor is built-in to the motherboard. The atom doesn't have much single thread oomph, but it does have 8 cores and all the features required to run a hypervisor, which might be worthwhile, especially if it turns out that the software programmable ethernet ports can be configured to manage all the routing on their own.
If I didn't already own this board, I'd probably pick up a similar Supermicro board that has six 10-gigabit ports on it. Right now there are a ton of used ones on ebay for around $80 per board, some including an E3-1200 processor in the $80 price. i.e. they cost even less than the pcengine board. Probably more than 20 watts TDP, but considering its a SuperMicro motherboard and each of the six ports supports RJ45 10gbe.... Heck, at that price for a 10Gbe node, I should buy 3 and build an HA ProxMox cluster.
@NeverDie Quite a lot of this thread is very interesting even though it all goes way over my head. Do you think one of these would do?
:}
